Understanding the Bastion Model in PAM Solutions: A Gateway to Secure and Simplified Access
In today’s digital landscape, organizations face increasingly complex security challenges. Sensitive systems and critical data are accessed by employees, contractors, and third-party vendors from different locations and devices. This distributed access landscape creates vulnerabilities that cybercriminals eagerly exploit.
To address these risks, many organizations turn to Privileged Access Management (PAM) solutions, and one key component gaining popularity is the Bastion model. But what exactly is the Bastion model, and why is it a game-changer for enterprise security and user convenience?
What Is the Bastion Model in PAM?
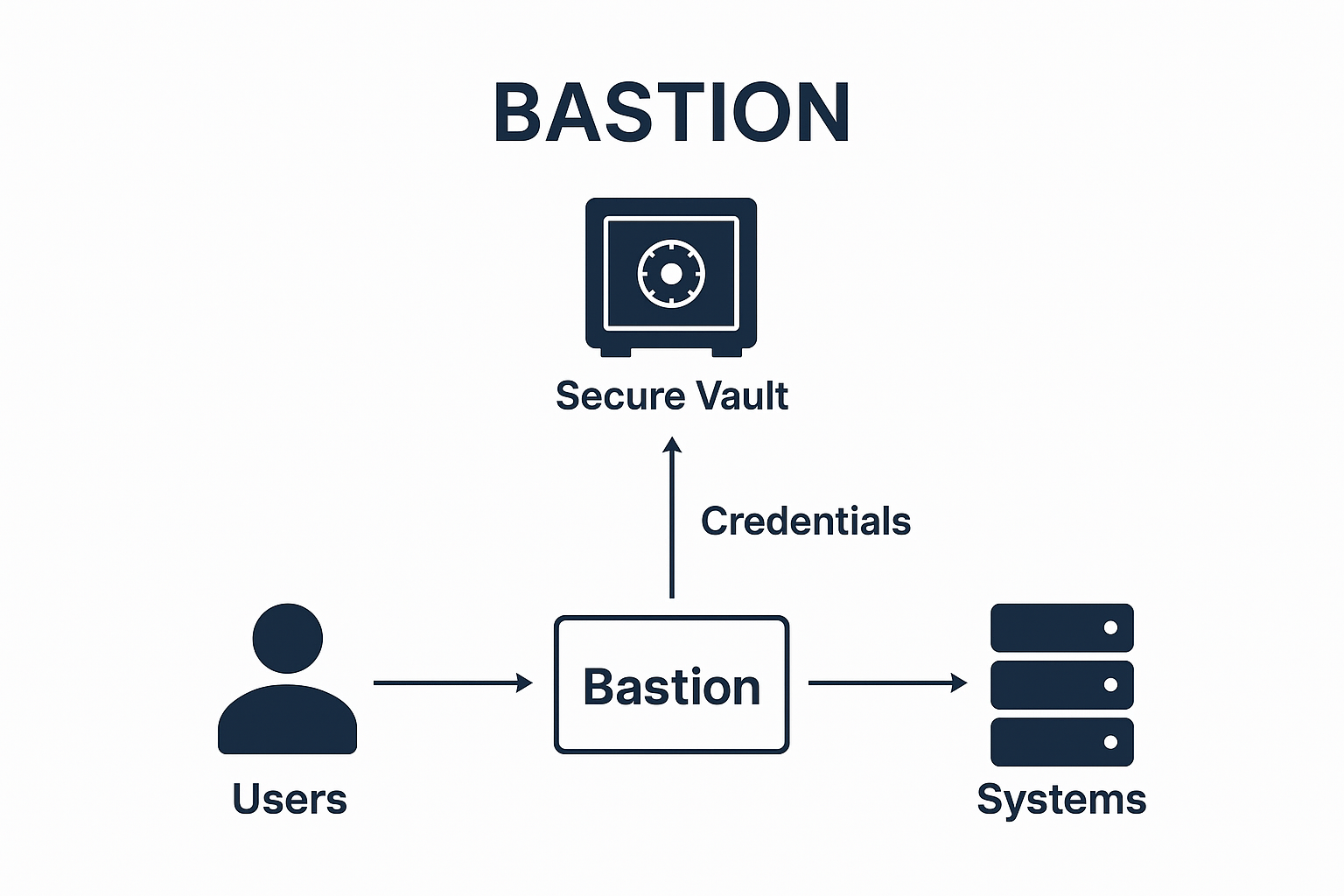
The Bastion model acts as a secure gateway between users and the sensitive systems they need to access. Rather than allowing direct connections to servers, databases, or applications, users connect first to the Bastion, which then brokers the connection.
Think of the Bastion as a “digital guard tower” every privileged session starts and ends here, creating a controlled, monitored, and auditable environment.
In the context of PAM solutions, the Bastion model typically integrates with features like:
-
Session management and monitoring
-
Credential vaulting (password safe)
-
Access approval workflows
-
Recording and auditing capabilities
Key Advantages of the Bastion Model
Enhanced Security with Credential Vaulting
One of the Bastion’s most powerful functions is storing privileged credentials in a secure password vault. Instead of users knowing or handling the actual usernames and passwords for critical systems, the Bastion manages them.
- This means:
Users never see sensitive passwords: they simply click to connect, and the Bastion injects the credentials automatically. - No more password leaks: because users can’t write them down, share them, or accidentally expose them in phishing attempts.
- Centralized control: administrators can rotate, revoke, or update passwords instantly across the infrastructure without disrupting operations.
Complete Visibility and Accountability
Every action taken via the Bastion can be logged and recorded. This provides:
-
Session monitoring: Security teams can observe live privileged sessions in real time.
-
Full audit trails: Every command, change, or access request is documented for compliance and investigation purposes.
-
Regulatory alignment: For industries under strict regulations (e.g., finance, healthcare, government), Bastion simplifies demonstrating compliance with standards like ISO 27001, NIST, or GDPR.
Simplified Access for Users
While security often comes with added complexity, the Bastion model does the opposite, it makes access easier for users.
Instead of juggling multiple usernames and passwords for different systems, employees simply log into the PAM solution and select the system they need. The Bastion handles the rest, providing passwordless access while maintaining strict security controls.
This removes friction for IT teams, contractors, and admins, allowing them to focus on their tasks rather than struggling with authentication processes.
Reduced Attack Surface
By forcing all privileged connections through a single secured gateway, organizations can:
-
Eliminate direct system exposure to the internet or internal users.
-
Enforce security policies consistently (e.g., MFA, session timeouts, IP restrictions).
-
Detect and respond to anomalies faster since all activity is centralized.
This containment strategy makes it significantly harder for attackers to move laterally within the network, even if they compromise one endpoint.
Streamlined Incident Response
Because the Bastion logs all privileged sessions and controls all access, it becomes much easier for security teams to:
-
Identify when and how an incident occurred.
-
Terminate or suspend risky sessions in real time.
-
Quickly rotate or revoke credentials without needing to touch every individual system.
How Does the Bastion Benefit Organizations?
For organizations, the Bastion model provides:
-
Stronger security posture: with centralized control over privileged access.
-
Operational efficiency: no more manual credential management.
-
Audit readiness: complete session records for compliance checks.
For users, it means:
-
Less hassle: no need to memorize or manage passwords for every system.
-
Faster access: one login, many systems.
-
Peace of mind: knowing they’re working in a secure, monitored environment.
Conclusion
The Bastion model is more than just a feature of modern PAM solutions, it’s a strategic approach to privileged access security. By acting as a secure gateway, vaulting sensitive credentials, and centralizing session monitoring, the Bastion creates a safer, simpler, and more accountable way for organizations to manage critical system access.
As cyber threats evolve, adopting PAM solutions with a Bastion architecture isn’t just a best practice it’s a necessity for any organization serious about protecting its most valuable digital assets.
Bastion Model Architecture Overview
Here is a simplified visual representation of how Gaterzone’s bastion architecture works: